INFORMATION SECURITY RESEARCH
and
DEVELOPMENT
Keeping Up The Good Work Since 10 Years
Developing Innovative Solutions To Keep You Safe
WE ARE ELIGIBLE!
Besides The R&D Projects We Completed During 6 Years
OSCP (Offensive Security Certified Professional) and OSCE (Offensive Security Certified Expert) are certifications that approve our eligibility.
WE KEEP THINGS EASY FOR YOU
OUR WAY OF SERVING:
A PROFESSIONAL SECURITY ORIENTED KNOWLEDGE
ROBUST

WE TAKE EXTRA CARE ON DEVELOPING
SYSTEMS THAT ARE ROBUST AND WORKS STABLE!
EASY TO USE

WE DEVELOP TECHNICALLY ADVANCED
BUT EASY TO USE SYSTEMS TO SAVE YOUR TIME
BUDGET FRIENDLY

WE DEVELOP TECHNICALLY ADVANCED
BUT EASY TO USE SYSTEMS TO SAVE YOUR TIME & MONEY
AUTOMATED

WE TAKE CARE OF HEAVY WORKS & DECISIONS
WE DEVELOP SYSTEMS THAT ARE EASY TO USE!
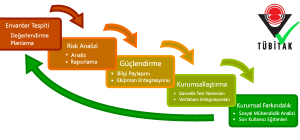
COMPLETED R&D PROJECTS
TINA – Advanced & PRO Protection
Advanced Threat Protection Models;
THREAT INTERCEPTING NETWORK APPLIANCE
AN AUTOMATED USER FRIENDLY SYSTEM
SECURITY ORIENTED
FREE FROM OPERATING SYSTEM AND PLATFORMS
INCLUDES HYBRID DETECTION TECHNIQUES; SANDBOX, HONEYPOT AND CYBER INTELLIGENCE COMBINED WITH UNIQUE PACKET INSPECTION ALGORITHM

ILDA
Developed against DoS attacks
ILDA detects and blocks attacks by dynamic analysis
ILDA (Intermediate Layer Defensive Application) provides successful protection on all layers from Layer 1 to Layer 7.
Capable of dynamic analysis, while ILDA Analyzer inspects the attacks on client servers actively, ILDA commander enables managing the attack traffic at Tier 2.
ILDA system provides successful defense at Layer 7 (software layer) for game servers, SaaS, application servers, unique software or services.

ISR Fuzzer
Apart from legacy fuzzers, ISR Fuzzer has it’s unique fuzzing methodologies.
This product currently is not in sale, but it is used for use in security projects and tests.

ScavDAT
ScavDAT is a penetration testing tool that is developed by ISR in order to follow the high standards during testing operation.
This product currently is not in sale, but it is used for use in security projects and tests.
Mena
MENA with it’s powerful intelligence center is ready to fight with cyber attacks.
Including multiple technologies; a router device with OpenWRT operating system and a powerful central database updated by machine learning, Mena product provides more security than a regular router.
7/24 auto-running CTM (Central Threat Management) powered by artificial intelligence technology and intelligence gathering mechanisms; offers contemporary technological advantages in malware analysis and detection.
– Completed Out of Sale R&D Projects –

Sonic5651
Sonic5651 is a Dell-SonicWALL compatible software that enables legal storage of DHCP logs according to Turkish laws.
Software is designed as an economic solution for logging, without buying additional devices.

SonicSpot
SonicSpot, is a Dell-SonicWALL compatible Hotspot solution that works integrated with UTM appliances.
Developed as a cloud service, it enables the easy and remote use of Hotspot authentication system in both guest and personnel networks.
System has SMS user authentication and Database integration capabilities.

KolaySpot
KolaySpot is a SaaS that enables user authentication controlling capability on appliances that are compatible.
By use of Cloud technology, without buying an additional appliance, KolaySpot can be run with your current Access Points, Modems or even cabled systems.
It is a framework especially developed for use of appliance manufacturers; enables adding extra features to their appliances with ease.
– Completed Out of Sale R&D Projects – Developed for Other Companies –

ProSpot
By developing the framework, ISR enabled ProSpot to be an economic cloud hotspot product.
System supports SMS user authentication, kiosk & voucher features, besides manual and central user management and database integration features.

Netsafe UTM & HotSpot
ISR is the former developer of NetSafe HotSpot ve NetSafe Unity UTM products.
NetSafe HotSpot Gateway, having integration capabilities with 3rd party database, hotel management systems and other features is developed for NetSafe Bilgi Teknolojileri A.Ş. that is owned and managed by Rhea Girişim Sermayesi Y.O. A.Ş. (Rhea Venture Capital Investment Trust). Project is completed and source codes are delivered to the management firm.

ZxSpot
ZxSPOT © is developed by ISR for E-Data Teknoloji Pazarlama Ltd. Şti. and ZyXEL Turkey.
ZxSPOT, is designed for working with all ZyXEL N4100 and UAG series. System delivers authentication information (user ID and password) via SMS and has integration capabilities with 3rd party database.
OUR CYBER SECURITY SERVICES
As experienced security professionals, we offer you our following services.

Advanced Penetration Test
We are not blackhat hackers, but we are following same lines when serving as red team!
Our advanced pentests includes waiting for days, sleepless, looking for and coding for exploiting the right vulnerability without getting caught to your security systems and policies.
Work schedule and roadmap depends on security level and precautions of the facility to be tested, main goal is to hack in to the systems, not to follow a regular road map.

Cyber Threat Interception
We are the best security team when we work together with you!
We analyse you well, we define your security concerns together. Evaluate them; check if they are true concerns and define the possibility of your concerns becoming to real life and cause a loss.
Just after the evaluation; we offer you the optimum solutions and discuss if your budget is ready or needs improvement. We plan your improvement moves, we improve both your human-based security abilities and technological protection abilities of your systems.
We do interfere in your security operations, as just as you need; not more, not less…

Security Appliance Test
We are here to prove your appliance is not secure!
Every security appliance has it’s own weaknesses, a security professional should know it’s own weaknesses and get related precautions and or developments, take the necessary risks.
We would love to check your new appliances, test their capabilities, check them against design failures, note their security levels and report the work we have done.

Penetration Test

Vulnerability Assessment

Application Security

Advanced Persistent Threat Detection

Source Code Review

Digital Forensic
3rd Party Software Audits

R&D Consultancy

Project Enhancement Support
Contact Us!
TURKEY
bilgi [ at ] isr.com.tr
TÜBİTAK Gebze Yerleşkesi Marmara Teknokent B-19
Gebze – KOCAELİ
U.S.A
sales [ at ] isr.com.tr
Lively Blvd. Elk Grove Industrial Park 2800, IL 60007
Chicago – ILLINOIS
Developing and Serving All Around The World
Some of Our Activities
02.03.2023
Meeting With Technology Enthusiastic Corporations on “Cube Incubation” Presentations, With Our New TINA Models & Technologies
08.06.2022

We Are Back In Our Stands Again!
02.02.2021

New Financing Options Available for License Purchases & Renewals
27.03.2020

We Are Open & Working Remotely During COVID Pandemic
15.01.2020


20.11.2019



20.11.2019


14.11.2019



06.11.2019



03.10.2019


06.08.2019


17.07.2019



12.06.2019



25.04.2019


03.04.2019


09.02.2019


26.01.2019


10.12.2018


31.10.2018


28.06.2018



19.04.2018


04.05.2018


25.04.2018



13.02.2018


27.11.2017



13.10.2017


07.09.2017



18.08.2017


28.04.2017


25.04.2017


30.03.2017

16.03.2017


27.01.2017
09.01.2017

![]()
09.01.2017
05.01.2017
Our New Office
We are moving our USA office to TTC, ELK Grove IL
05.01.2017
ARGONNE LAB VISIT



10.10.2016

We are expending our user number and Tina references.
Please feel free to contact us for any questions about Tina or for a Demo request.
23.09.2016


06.09.2016


22.08.2016

“Cyber Security Awareness Day”

23.05.2016

“Demo Day”

03.12.2015













